"Check out my new Iphone, It's using a 64 bit ARM. Not sure what it does but cool"
"My latest Samsung is using triple core processor. It's fast."
Unless you have direct benefits from using such devices with that features, you are nothing more then just a mere human being consumed by the homogenization of modernity.
This is the second part of Chromecast Experience. How does Chromecast work?
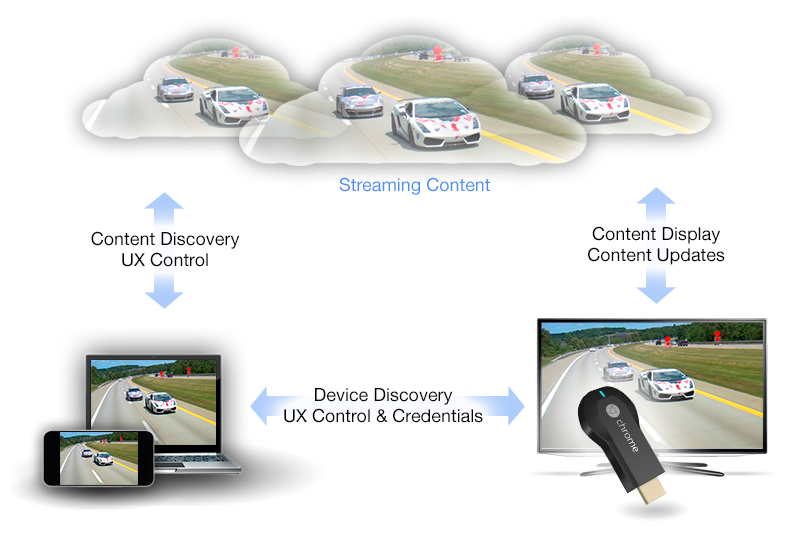
From Chromecast Developer Guide they have make a beautiful picture out of it.
"My latest Samsung is using triple core processor. It's fast."
Unless you have direct benefits from using such devices with that features, you are nothing more then just a mere human being consumed by the homogenization of modernity.
This is the second part of Chromecast Experience. How does Chromecast work?
From Chromecast Developer Guide they have make a beautiful picture out of it.
So how does Casting works? When you first boot in your Chromecast, A Web Services would run and listen at port 8008. From a Blackbox point of view it's probably a heavy modifcation of node.js . Most likely with RESTful implementation. of Web API. Owh it's using the DIAL .
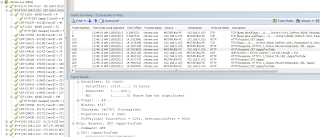
So how does it works? Let's run our sniffer. Many people would prefer tcpdump or wireshark. But hey Windows does it charmed with Microsoft Network Monitor. Coolest thing bout this tool is you can filter it by apps in this case we filter chrome.
Each time we issue a cast we actually "dial for it". When casting to a youtube application. We will send GET Request to /app/YouTube
And the information that we will retrive is in a form of an XML Format hinting the DIAL implementation in chromecast.
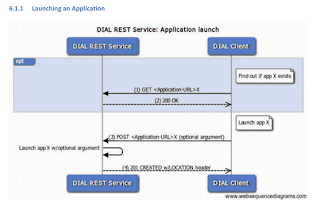
From the DIAL developers guide
The rules of Dial Service..
1. First we send the a dial request for the Application(Youtube, Netflix)
2. Dial Server response with Okay
3. Then We Post the Application URL in json format . It's actually a URL Forwarding technique.
4. Dial Server response . (Chromecast will launch it's Request via GET/POST to netflix or youtube).
At any application launch. The Apps can be kill (Netflix or Youtube) by issuing a HTTP DELETE.
Common HTTP Request can be found in the DIAL Developer Manual. Fiqueet.com have list down common Request that you can do with curl example.
get device information xml:
curl http://x.x.x.x:8008/ssdp/device-desc.xml
curl http://x.x.x.x:8008/ssdp/device-desc.xml
get detailed device information json:
curl http:///x.x.x.x:8008/setup/eureka_info?options=detail
curl http:///x.x.x.x:8008/setup/eureka_info?options=detail
scan for available wifi:
curl http:///x.x.x.x:8008/setup/scan_results
curl http:///x.x.x.x:8008/setup/scan_results
get supported time zones:
curl http:///x.x.x.x:8008/setup/supported_timezones
curl http:///x.x.x.x:8008/setup/supported_timezones
get info about current app:
curl -H “Content-Type: application/json” http:///x.x.x.x:8008/apps/YouTube -X GET
curl -H “Content-Type: application/json” http:///x.x.x.x:8008/apps/YouTube -X GET
Which get back to us.. How does the video were streamed to us? Here is an incorrect pseudo-diagram but sufficient enough.
By now you should have at least an idea how to bypass it. If not you can wait for Part 3.


No comments:
Post a Comment